WannaCry: What is ransomware and how to avoid it
What you need to know about ‘WannaCry’, the malicious software behind Friday’s worldwide hacking attack.
Malicious software or “ransomware” has been used in a massive hacking attack, affecting tens of thousands of computers worldwide.
Software security companies said a ransomware worm called “WannaCry” infected about 200,000 computer systems in 150 countries on Friday, with Russia, Ukraine, and Taiwan being the top targets.
Keep reading
list of 4 itemsHong Kong’s first monkey virus case – what do we know about the B virus?
Why will low birthrate in Europe trigger ‘Staggering social change’?
The Max Planck Society must end its unconditional support for Israel
The hack forced British hospitals to turn away patients, affected Spanish companies such as Telefonica, and threw other government agencies and businesses into chaos.
Cyber security researchers from Symantec and Kaspersky Lab have said that some code in an earlier version of the WannaCry software had appeared in programmes used by the Lazarus Group, which researchers from many companies have identified as a North Korea-run hacking operation.
“This is the best clue we have seen to date as to the origins of WannaCry,” Kaspersky Lab researcher Kurt Baumgartner told Reuters news agency on Monday.
READ MORE: Global cyberattack alert as experts warn of more havoc
Here is what you need to know about the software behind the global cyber-attack.
How it works:
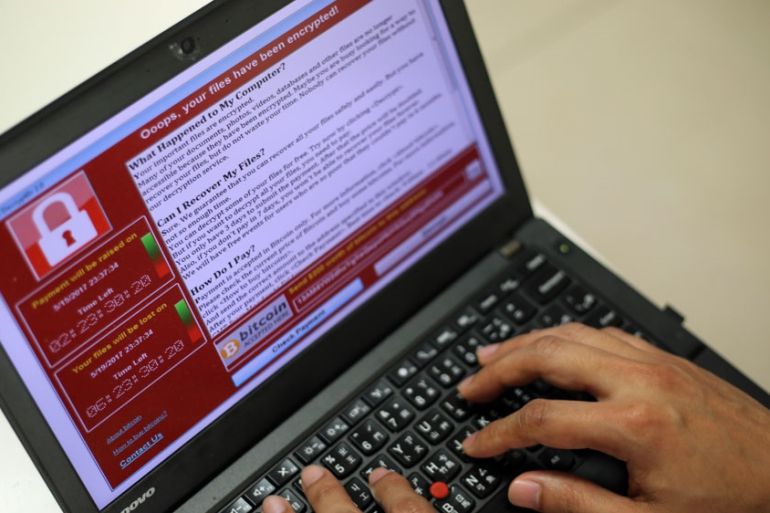
WannaCry is a form of ransomware that locks up files on your computer and encrypts them in a way that you cannot access them any more.
It targets Microsoft’s widely used Windows operating system.
When a system is infected, a pop-up window appears with instructions on how to pay a ransom amount of $300.
The pop-up also features two countdown clocks; one showing a three-day deadline before the ransom amount doubles to $600; another showing a deadline of when the target will lose its data forever.
Payment is only accepted in bitcoin.
The ransomware’s name is WCry, but analysts are also using variants such as WannaCry.
A hacking group called Shadow Brokers released the malware in April claiming to have discovered the flaw from the US’ National Security Agency (NSA), according cyber-security providers.
How it spreads:
Ransomware is a programme that gets into your computer, either by clicking or downloading malicious files. It then holds your data as ransom.
Some security researchers say the infections in the case of WannaCry seem to be deployed via a worm, spreading by itself within a network rather than relying on humans to spread it by clicking on an infected attachment.
![A number of hospitals operated by Britain's National Health Service (NHS) were hit by the ransomware cyberattack, causing failures to computer systems [Will Oliver/EPA]](/wp-content/uploads/2017/05/e9425debba474cf188b98c5e7f6bbbdd_18.jpeg)
The programme encrypts your files and demands payment in order to regain access.
Security experts warn there is no guarantee that access will be granted after payment.
Some forms of ransomware execute programmes that can lock your computer entirely, only showing a message to make payment in order to log in again.
Others create pop-ups that are difficult or impossible to close, rendering the machine difficult or impossible to use.
Where it has spread:
Researchers with security software maker Avast said Russia, Ukraine, and Taiwan were the top targets of the attack, but dozens of other countries also reported system infections.
James Scott, from the Washington DC-based Institute of Critical Infrastructure Technology, said ransomware emerged “as an epidemic” back in 2016. He said the healthcare sector was particularly vulnerable because of poor digital security knowledge.
“The staff have no cyber-hygiene training, they click on phishing links all the time. The sad thing is they weren’t backing up their data properly either, so that’s a big problem. They should be doing that all the time,” Scott told Al Jazeera.
“Everyone’s vulnerable right now because you’re only as strong as your weakest link within your organisation from a cyber-perspective.”
What can you do to prevent infection:
According to Microsoft’s Malware Protection Center, here are the steps you should take to protect yourself against ransomware:
– Install and use an up-to-date antivirus solution (such as Microsoft Security Essentials)
– Make sure your software is up-to-date
– Avoid clicking on links or opening attachments or emails from people you don’t know or companies you don’t do business with
– Ensure you have smart screen (in Internet Explorer) turned on, which helps identify reported phishing and malware websites and helps you make informed decisions about downloads
– Have a pop-up blocker running on your web browser
– Regularly backup your important files
WannaCry ‘kill switch’
On Saturday, a cybersecurity researcher told AFP news agency that he had discovered a “kill switch” that can prevent the spread of WannaCry.
The researcher, tweeting as @MalwareTechBlog, said the discovery was accidental, but that registering a domain name used by the malware stops it from spreading.
Unfortunately computers already affected will not be helped by the solution.
@MalwareTechBlog warned that the “crisis isn’t over” as those behind it “can always change the code and try again”.
“I will confess that I was unaware registering the domain would stop the malware until after I registered it, so initially it was accidental,” @MalwareTechBlog tweeted.
“So long as the domain isn’t revoked, this particular strain will no longer cause harm, but patch your systems ASAP as they will try again.”
|
|